In this post, I'll discuss about the basics of keytab file and the procedure to create a keytab file:
1) Keytab is a file that contains kerberos principal and encrypted key
2) You can authenticate to kerberos using keytab
3) If you changed your kerberose password then you need to create a new keytab file
4) Keytab file is used in scripts to automate kerberos authentication or by some service accounts
We can create keytab file using 2 ways:
----
Using ktutil command
From kadmin console
----
Note: Before reading further, please go through the below post and get a basic idea on MIT kerberos.
http://www.maninmanoj.com/2018/04/mit-kerberos-installation-and.html
Scenario 1: Creating the keytab file using kadmin from the KDC server. The steps are highlighted in the below snapshot:
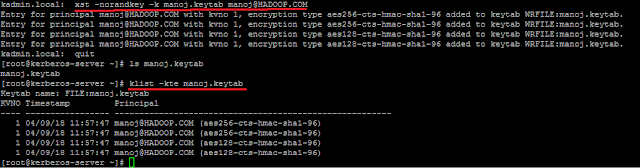
1) Create a principle as manoj@HADOOP.COM from kadmin.local.
2) The name of the keytab created is manoj.keytab for the principle manoj@HADOOP.COM using ktadd command. This can be created as below:
Note: norandkey is used so that the password for the principle manoj@HADOOP.COM is not changed.
3) logout of the kadmin shell and using the below command we can initialize the principle without password
kinit -kt manoj.keytab manoj@HADOOP.COM
whereas directly using kinit to the principle name will show password prompt:
Scenario 2:Using ktutil from the client machine create the keytab for the principle manoj@HADOOP.COM here we need to mention the encryption type as mentioned in the /etc/krb5.conf.
The encryption types used here as below:
des3-cbc-sha1-kd
arcfour-hmac-md5
des-hmac-sha1
des-cbc-md5
des-cbc-md4
Use "wkt" command to write the keytab to the desired location, here I've written to the location /tmp/manoj.keytab.
Now, you will be able to see the details of manoj.keytab as below and you can kinit using the keytab without password.
Scenario 3: Creating keytab using ktadd but not using the option "norand" key. This will overwrite the password of the user principle manoj@HADOOP.COM. This should never be used in production environment as this will replace the exiting password to a new random encrypted password.
Reference:
https://www.youtube.com/watch?v=_TyNUign4Ko&list=PLY-V_O-O7h4fHTSxNCipvqfOvFCa-6f07&index=19
https://www.ibm.com/support/knowledgecenter/en/SSZUMP_7.1.2/management_sym/sym_kerberos_creating_principal_keytab.html
1) Keytab is a file that contains kerberos principal and encrypted key
2) You can authenticate to kerberos using keytab
3) If you changed your kerberose password then you need to create a new keytab file
4) Keytab file is used in scripts to automate kerberos authentication or by some service accounts
We can create keytab file using 2 ways:
----
Using ktutil command
From kadmin console
----
Note: Before reading further, please go through the below post and get a basic idea on MIT kerberos.
http://www.maninmanoj.com/2018/04/mit-kerberos-installation-and.html
Scenario 1: Creating the keytab file using kadmin from the KDC server. The steps are highlighted in the below snapshot:
1) Create a principle as manoj@HADOOP.COM from kadmin.local.
2) The name of the keytab created is manoj.keytab for the principle manoj@HADOOP.COM using ktadd command. This can be created as below:
Note: norandkey is used so that the password for the principle manoj@HADOOP.COM is not changed.
3) logout of the kadmin shell and using the below command we can initialize the principle without password
kinit -kt manoj.keytab manoj@HADOOP.COM
whereas directly using kinit to the principle name will show password prompt:
The encryption types used here as below:
des3-cbc-sha1-kd
arcfour-hmac-md5
des-hmac-sha1
des-cbc-md5
des-cbc-md4
Use "wkt" command to write the keytab to the desired location, here I've written to the location /tmp/manoj.keytab.
Now, you will be able to see the details of manoj.keytab as below and you can kinit using the keytab without password.
Scenario 3: Creating keytab using ktadd but not using the option "norand" key. This will overwrite the password of the user principle manoj@HADOOP.COM. This should never be used in production environment as this will replace the exiting password to a new random encrypted password.
Reference:
https://www.youtube.com/watch?v=_TyNUign4Ko&list=PLY-V_O-O7h4fHTSxNCipvqfOvFCa-6f07&index=19
https://www.ibm.com/support/knowledgecenter/en/SSZUMP_7.1.2/management_sym/sym_kerberos_creating_principal_keytab.html





No comments:
Post a Comment
Note: only a member of this blog may post a comment.